July 2004Trading Tip:
Straddle-Strangle-Swap
by Bill Hatch
One of the common strategies for options trading is the 'Iron
Condor'. In the case of a short condor, the trader goes long
on the greatest strike in a vertical call spread and the lowest
strike in a vertical put spread. The trader then shorts on the
middle strikes for both the call and the put. This is a Bear
call spread and a Bull put spread. The maximum gain is reached
when the options expire in the center of the short options.
The trader keeps the total of the premiums received.
As an example, XYZ Iron Condor would be:
- Long $70
call Note:
Legs 1 and 4 are 'buying a strangle'.
- Short $65 call
Note: Legs 2 and 3 are 'selling a straddle'.
- Short $60 put
- Long $55 put
Historically, this has been a successful trading strategy for
stocks that do not move much. In effect, you sell time.
The passage of time is the one absolute certainty in the
market. Iron Condors are good for stocks expensive enough to
warrant a $5 strike increment.
Tom Sawsnaw of http://www.thinkorswim.com/
taught me a variation of the condor that has worked well.
(That really means Tom came up with the idea, I claim no
credit. Tom told me that his clients using this strategy make
money routinely. He likes that because he gets more
commissions.) The steps are:
- Find a stock that does not move much, but has a $2.50 strike
increment.
- Buy a 'strangle' with a life span of several
months.
--Buy a higher
Call (leg 1) and buy a lower Put (leg 4).
- Sell a 'straddle' for the current
month.
--Sell a
middle Call (leg 2) and sell a middle Put (leg 3).
- If the market moves against the straddle, you have your
insurance, and will not loose more than the $2.50 minus premiums
received for the straddle.
- Re-sell the straddle monthly. This is an important key
to making a profit.
- The optimum action is to buy back the leg that threatens an
exercise.
- The easiest way to buy back the straddle leg is to sell a
calendar spread. I personally like to sell both legs to
eliminate any possibility of a last minute exercise. I was
once exercised on Home Depot with $0.03 difference between the
strike and the price of the stock.
I call this a 'Straddle-Strangle-Swap'. The name describes
the process, but here is an example of how it works from my own
experience:
- After May Expiration, I bought a November $32.50/$37.50
strangle for Dell for $2.05.
--Long a
Call @ $37.50 and Long a Put @ $32.50.
- I immediately sold a June $35 straddle for
$1.50.
--Short a Call @ $35 and Short
a Put @ $35.
- As June expiration approached, I sold calendar spreads for
both the $35.00 call and put for a total of
$1.45.
--Bought back the June Call and Put and replaced them by selling a
July Call and Put.
- Yesterday morning, I sold the same calendar spreads for
$1.70. I probably could have waited to get another nickel,
but 'pigs get
slaughtered'.
--Bought back the July Call and Put and replaced them by selling
an August Call and Put.
I still have August through November to do the same thing, and
when November does come, I will have a classic Condor. So far,
with $2.05, my net is + $4.65 ( = $1.50 + $1.45 +
$1.70). I still have four more months to collect. AND, I
have the asset of the strangle. If the market repeats
history, I will net over 500% on the initial expense of the
strangle. Optimally, as November expiration nears, I will buy
a LEAP calendar spread on the two strangle legs and continue the
same process.
I have been successful using this strategy with Dell,
Home Depot, Office Depot, AMD and Disney. My bad month with
Disney was the single month covering the Roy Disney retirement, the
litigation against their CEO, Michael Eisner, and the Disney/Pixar
estrangement.
I have found that it is usually a good practice to wait until
expiration week to do any trading out of the leg that moves against
me. Most traders will not exercise while there is still
extrinsic time value. Within the last week, Dell lost almost
two dollars to come back down to the $35.00 strike
neighborhood. I saved my profit by being patient.
Question: 'I have a question for Bill Hatch who
wrote the article. I understand the technique as presented,
you explained it quite well. However, I'd like to know what
you might suggest if the price of the underlying goes up or down
during the time period of the strangle. Example: Let's assume
the scenario that you presented in the newsletter with Dell
stock. But what if Dell rises above the original strangle at
the time of the front month straddle expiration? What if Dell
were to rise to $38.50 putting the long back month Call in the
money? Would you go flat on both the strangle and straddle and
start all over again at a higher mid-price? Or, would you hold
onto the back month strangle and adjust the new front month straddle
strike? Or, would you still be using a $35 straddle
strike? Thanks again for the very intriguing article, I
believe I'll be trying this strategy quite soon to see how it works
out for me. I really appreciate any input you might
have.' -S. Miller 07-28-2004
Answer: 'Going beyond the strangle has happened to
me on two occasions. In both I waited until early on
expiration week and sold a calendar spread; ie bought an August call
and sold a September Call. I was still able to take advantage
of the time value in the option and reduce the potential loss.
I mentioned a loss on Disney when I described the strategy. In
the case of Disney, my strangle expired on the following
month and I finally ended up just eating my loss the following
month on Disney. By selling the extra calendar spread, I
minimized and really came out positive because of the previous
months I had been able to sell straddles. In the other
experience, Home Depot moved down to the expected strike of the
straddle and I was able to continue as if nothing had
happened. There was no real downside, but when the stock
price is $2.50 higher than the strike of a Put, a Put
calendar spread has little value, so I was only able to capitalize
on half of my planned straddle sale. I waited until the value
went down a little and got half of the month of extrinsic value by
selling that Put later. I hope this helps.' -Bill Hatch
An example stock option model is shown in the August
Trading Tips issue.
For more information on the definition of a 'strangle' and a
'straddle', read the lesson materials on this web site: http://www.thinkorswim.com/tos/displayPage.tos?webpage=lessonStraddle
Trading Tip:
Forex Trading
by Larry
Pesavento
Forex trading is the epitome of liquidity when the major foreign
currencies are included. Price swings are fast and
large! These are ideal conditions for a pattern recognition
swing trader. Swing trading defines price swings from a few
minutes to a few days. Pattern recognition refers to the
probability of certain patterns repeating consistently. Pattern
recognition has always had a strong following among technicians but
a recent book by Dr. Andrew Lo, ‘The Non Random Walk Down Wall
Street’ studied over 30,000 chart patterns over 30 years and found
startling correlations from the standard chart patterns such as head
and shoulders, double tops and bottoms, pennants, flags and island
reversals. The results were so amazing that Business Week
featured Dr. Lo’s work in the April 17, 2000 issue, soon after CNBC
and Bloomberg began increasing the coverage of technical analysis
techniques. Even the “F” word, Fibonacci, is used commonly by
reporters.
My favorite Forex trading vehicles are the Euro currency,
Japanese Yen and British Pound. I do very little cross rate
trading although the patterns I use work quite well in these
markets.
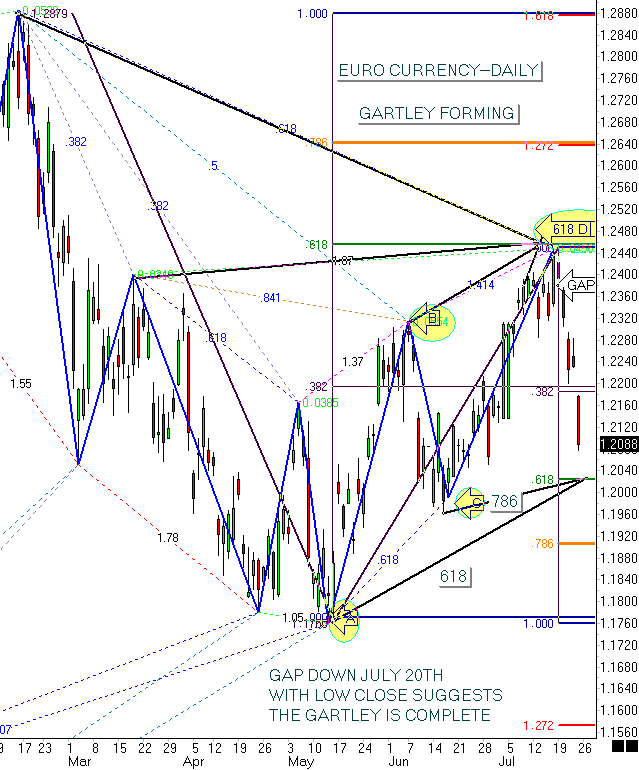
There are no secrets to Forex trading in my opinion. They
are active and liquid and provide pattern recognition swing trading
opportunities. The best place to start learning about Forex
trading is from the 30-minute continuous charts. Find the most
common swing on that chart. From this starting point you can
take every other swing on the 30 minute chart and relate it to one
of five ratios: 0.618, 0.786, 1.00, 1.272 and 1.618. These
five ratios will describe nearly all of the swings you can see on a
30 minute chart.
Next find similar time counts such as four hours up – four hours
down for example. Charts reveal many secrets if you study them
religiously. Also watch for similar time frames between highs
and lows. Printing out the chart and drawing in the price
swings and connecting all swings to all other swings will reveal
patterns you never thought existed.
A word of caution – you can find the best patterns that ever
existed and you will still lose money if you don’t know how to
control risk. Winners focus on how much can be lost and losers
focus on how much they can win! Have you ever seen a slot
machine that says – “I’ve taken in 1 million dollars this year” –
not a chance!
The best exercise you can do for yourself as a trader is to read
3 or 4 pages of Mark Douglas’ book ‘Trading in the Zone’ each day
before you start trading. This will act like an anchor each
day to focus on thinking in probabilities not certainties. At
the end of the year you will have read the entire book twice!
Computer Tip:
Computer Issues
by
Mike Lamont
Virus
A virus is a program that attaches itself to another programs and
executes along with its host. The end result is as varying as
its author’s imagination. Many viruses, for the most part, run
unbeknownst to the user and are malicious and destructive, wreaking
havoc on the hosts computer even so far as crashing it an causing
all of the data to be lost.
Viruses can be transmitted through mediums like disks, CD’s,
emails, attachments, web sites, etc. Some viruses are
self-perpetuating. For instance, an email virus may attach
itself to your email and send the virus to every address in your
email phone book.
A good virus detector is suggested and updates of the virus
definitions done at least daily. Currently, my virus detector
has 67,806 viruses it tests for. Many are created each and
every day.
This is a quote from Symantec (authors of Norton
Anti-Virus). The whole article may be found here: http://securityresponse.symantec.com/avcenter/reference/newsletter/Apr04inews.html
As in previous months,
multiple medium- to high-risk worm outbreaks, based on the MyDoom,
Netsky, and Beagle worm families, dominated March and April.
However, the DeepSight Threat Analyst Team released a Threat Alert
in March on W32.Witty.Worm. This worm exploits the Internet Security
Systems Protocol Analysis Module ICQ Parsing Overflow vulnerability,
also released that month. W32.Witty.Worm is entirely memory resident
- no files are created or dropped. Its payload is especially
destructive, since it writes random data to physical disks, causing
data corruption on the hard drives of the infected computer.
On April 13th, Microsoft released three Security Bulletins, which
address 18 new vulnerabilities and included updates for three
existing vulnerabilities:
- MS04-011 provides a Security Update for Windows that rectifies
14 new vulnerabilities, many of which are highly critical.
- MS04-012 is a Cumulative Update for Microsoft RPC/DCOM
Security and details 3 new vulnerabilities and 1 previously known
vulnerability.
- MS04-013 provides a cumulative patch for Microsoft Outlook
Express that addresses two new vulnerabilities.
April 30th saw the release of the first version of the Sasser
worm. W32.Sasser.Worm is a blended threat that attempts to exploit
the LSASS vulnerability, described in Microsoft Security Bulletin
MS04-011. It spreads by scanning randomly selected IP addresses for
vulnerable systems. This worm and its variants are estimated to have
infected millions of PCs worldwide. See later in the Newsletter for
more details on the worm and the LSASS vulnerability.
Worm
A worm is specific type of virus. One big difference is a worm
propagates itself as it "bores" its way through computers and
networks. These copies then branch off and continue the
destructive propagate and destroy process. Recently some worms
crashed parts of the Internet or brought it to a sluggish
crawl. Many virus detectors can detect many worms depending on
the way they infect your computer. Many, however, bypass virus
detectors all together.
The best way to keep worms out is keeping your operating system
up-to-date. Many worms exploit weaknesses in communication
protocols and become available for worm infections.
Another way to protect against worms is a firewall. This
will keep all unwanted activity from leaving or entering your
computer (as long as your operating system is up-to-date).
Macro
Macros are mini script programs that are run in host programs to
simplify and augment functionality. However, malicious macros are
viruses that can do anything an author’s devious mind comes up with.
Many macro viruses come in email attachments. It is best to
not open any email attachment unless you are absolutely certain of
its validity.
Make sure you have a good virus detector and that it is capable
of detecting macro viruses.
Trojan Horse
These are aptly named. They appear to be one thing,
harmless and normal, but actually are deceptive and dangerous.
They are meant to obtain and deliver information from your computer
to the developer. Many Trojan Horses can actually send keyboard
input as well as mouse-clicks. This means, when you log on to
your on-line banking and type in your username and password, this
information can be transmitted to the author and they can then log
into you bank account if they wish. This is only one example
of the very serious threat these Trojan Horses are.
Virus Detectors and Firewalls are the best means of
protection.
SpyWare
These are currently legal Trojan Horses. These are
meant to help advertisers in obtaining your Internet activity
to how to send advertisements (eg. Popups, spam, etc.) to you.
My wife shops online for kids clothes, shoes, etc. She would
receive popups and spam from these types of companies I, on the
other hand, browse for programming code, drivers, dll’s, etc.
I would receive popups from those types of companies. For
SpyWare companies, this information is invaluable as you can
see. Why would my wife want spam on new companies with TCP/IP
drivers? This begs the question, why would anybody of any
semblance of sanity want any spam to begin with?
The best protection of these types of programs is SpyWare
killers. We use AdAware from LavaSoft:
http://www.lavasoftusa.com/
This does not get all of them, but for our purposes, it is
sufficient.
Windows Updates
It is imperative to keep your windows updated. They are
free and easy. In fact, I have mine set to automatically check
download and install the updates. Many fixes and critical
updates are security breaches that worms have honed in on. By
staying current, you are staying as safe as you can be. To
manually update windows, you can:
- Click on Start | Windows Update
- Go to http://www.microsoft.com/ and
click Windows Update (on the left of the screen)
- Set your system to automatically check and install updates
Virus Detector
A program that runs real-time and checks incoming email
attachments, file downloads, file installs, files on you computer,
etc. If a virus is detected, many times it is simply
deleted. Sometimes more serious efforts are needed, depending
on the virus. It is suggested that the virus detection table is
updated often (at least once a day) as many new viruses are detected
each day.
Firewall
This is a program, device or other mechanism that protects you
computer from outgoing or incoming data. Imagine a castle with a
mote. Nothing can get into the castle except by the heavily
guarded drawbridge. Anything that the guards deem as unwanted,
they are thrown into the mote with the mote monster. A
firewall does the same type of thing. Any activity (eg. Email,
ping, browse, tcp/ip, etc.) is not allowed unless you tell the
firewall to allow it. Some types of firewalls are:
- Software on your computer (like ZoneAlarm: http://www.zonealarm.com/)
- Router
- Switch
- Hub
- Computer
- Linux Box
- Firewall box
- Proxy Server
Now, say your system has a worm. My ZoneAlarm has caught
one of these. ZoneAlarm will say something to the affect,
"Windows Media Player wants to access the web at: …) and give an
address and a port. Note, the name seems legitimate, but it is
misspelled. Many even are spelled correctly. If I was to
allow this to access the Internet, then I have assisted in its
propagation. Now, this is confusing because the legitimate
Media Player does need to access the Internet. As you can see,
this becomes daunting very quickly. My firewall has "More
Info" and "Help" buttons that gets a good workout when I note
something I am not familiar with.
Whole companies are built on Internet security. This area
can be as easy or as complex as you want it to be.
A good firewall, SpyWare killers and virus detectors have become
as much a necessity as a monitor and keyboard. The amount of
security you apply to your system is up to you. Some simple
steps may be sufficient. The computer is a tool just a wrench
is to a mechanic and a scalpel is to a surgeon. It is expected
that a mechanic know how to use the wrench and the surgeon is
expected to know how to use the scalpel, we need to know how to use
our computer – the tool of our trade. Sure, we plug it in and
it works, but knowing some of these basic ideas will keep you
safer.
Even with good security, it is still possible for these sneaky
culprits to sneak in. When they do, as they have in my case,
downtime is immeasurable. I have been down for as much as one
day to a couple weeks and I find myself focusing on getting the
system back up and all the information I lost rather than my
trade. This brings me to my last item:
Backups
Backing up data is vitally important. Who knows when a hard
drive will decide to crash? Who knows when a lightening strike
or power outage will cause your system to fry? Who knows when
your computer will be stolen? We have a saying in this support
office:
There are four types of people:
- Those that don’t backup.
We talk to people that have
no backups at all. They call us and inform us that their
hard has drive crashed. (Please note that most hard drives
only last 7 to 10 years.) There is absolutely nothing we nor
they can do. I’ve been there. It is a sickening
feeling. Years of work down the drain and not a single thing I
could do.
- Those that don’t backup yet.
Anybody that has not
backed up and crashes, soon become folks that backup.
Unfortunately it takes a terrible crisis to get them to do
this. Hard disks, and other mediums are so cheap now days
that not backing up is just not wise.
- Those that don’t backup often.
Before I do any
programming, I make a backup. As I make milestones in the
programs I work on, I save and backup again (sometimes as many as
ten times a day). When I finish, I make a final
backup. Some folks that call our office have backups from
1993 (true story). What good is that going to do for data
today? Daily, weekly and monthly backups are necessary.
Again, this is the tool of your trade. Make sure you take
proper care of it.
- Those that don’t check their backups.
Checking your
backup is vital. We had a company that made a backup
everyday after we trained them how to do it. A year later,
their computer was stolen. They bought a new one and
installed the software. They took their last backup and it
did not work. They were successful in installing our backup
(thank goodness) from a year ago, but every backup they had done
(over 300) was not good. They were doing it wrong.
They ended up putting in weeks of effort to rebuild their
databases one-by-one. Check your backups.
The following is an ESPL program that will do a backup for you
simply by clicking the Run = 0 button.
- Open your ESPL script Editor (File | Open | ESPL Editor
- Click the New button
- Paste this in the script window
- Click on the ESPL Menu
- Click on Save As
- Type in Backup
- Press the Save button
- Hit the Run button
You will notice a DOS Window icon will appear minimized on your
taskbar. If you wish, you can click on it and notice the
various files being copied.
/*********************************************************
Written
by Mike LaMont (7/14/04)
The following program does a backup of
the entire Ensign
Folder.
**********************************************************/
procedure Backup;
var iStatus: integer;
begin
iStatus := WinExec('xcopy "' + // Microsoft XCOPY command
sPath
+
// Current Ensign path
'*.*" '
+
// All files
'"C:\EnsignBackup\'
+ // Make the
Backup Folder
FormatDateTime("yyyymmdd", Now) + '" /e /i
/r /y');
if (iStatus <= 31) then ShowMessage("Error
executing backup.");
end;
begin
if ESPL = 0 then Backup;
end;
|